Introduction: The High Stakes of Software Security
Security is foundational, not optional. Developers, not just IT security teams, are responsible for preventing breaches that can cost millions and shatter trust. From misconfigurations to outdated libraries, small gaps can have devastating consequences.
The Cost of Ignorance: Real-World Breach Stories
🚨 Equifax (2017) - The Patch That Never Came
| Issue: | Apache Struts vulnerability left unpatched [ Read more] |
| Impact: | 147 million Americans affected; over $700 million in settlements |
| Lesson: | Always patch known vulnerabilities and monitor dependencies |
🔥 Target (2013) - A Vendor's Weak Link
| Issue: | HVAC vendor credentials compromised [ Read more] |
| Impact: | 40 million credit card numbers, 70 million records leaked |
| Lesson: | Implement network segmentation and strict vendor access controls |
🛠 SolarWinds (2020) - Supply Chain Sabotage
| Issue: | Malicious code inserted into software update [ Read more] |
| Impact: | Government agencies and large companies compromised |
| Lesson: | Secure your build pipeline and validate update sources |
⚠️ Capital One (2019) - The Cloud Misconfiguration Fallout
| Issue: | SSRF vulnerability exposed via misconfigured AWS WAF [ Read more] |
| Impact: | Over 100 million records leaked |
| Lesson: | Infrastructure security is as critical as application security |
🔑 Uber (2016) - Secrets in the Code
| Issue: | Hardcoded AWS keys in public GitHub repo [ Read more] |
| Impact: | $100K fine and reputational damage |
| Lesson: | Never hardcode secrets; use secret management tools |
Common Causes of Breaches & How to Prevent Them
| Best Practice | Real-World Example | Lesson Learned |
|---|---|---|
| Validate and Sanitize All Inputs | A fintech developer blocked a stored XSS attack in a feedback form using input validation. A similar XSS vulnerability in Google Cloud exposed user risk before being patched. | Always validate and sanitize user inputs—never rely solely on client-side validation. |
| Use Secure Storage for Credentials | A junior dev leaked AWS keys in GitHub. Uber suffered a similar breach where hardcoded secrets led to a $100K fine and public backlash. | Use secret managers and tools like git-secrets to avoid committing sensitive
credentials. |
| Apply the Principle of Least Privilege | Capital One’s breach involved over-permissive IAM roles, allowing an attacker lateral access through SSRF. | Enforce minimal privileges by role and eliminate unnecessary access to sensitive data. |
| Shift Security Left with DevSecOps Tools | GitHub’s token scanning and Dependabot helped prevent dependency-related exploits early in CI pipelines. | Automate vulnerability checks at the pull request stage to reduce exposure windows. |
| Embrace Automated Security Testing | SonarQube scans discovered SQL injection flaws in popular open-source tools before real-world exploitation. | Regularly scan legacy and live code for hidden security debt using SAST tools like SonarQube. |
How Developers Can Make a Difference

How Developers Make a Difference – Real-World Examples
| Best Practice | Real-World Example | Lesson Learned |
|---|---|---|
| Validate and Sanitize All Inputs | A fintech developer blocked a stored XSS injection in a feedback form using regex validation and sanitization. A competitor later suffered a similar successful attack due to lack of input checks. | Always validate and sanitize user inputs, even with client-side validation in place. |
| Use Secure Storage for Credentials | A junior dev accidentally committed AWS keys to GitHub. Bots used them to run crypto miners, causing a $10,000+ bill. | Use secret managers like AWS Secrets Manager or Vault. Prevent secrets in code with tools like
git-secrets. |
| Apply the Principle of Least Privilege | A disgruntled intern with broad IAM access leaked customer data from a dashboard only meant for the support team. | Enforce "need-to-know" access. Scope IAM roles tightly based on user responsibilities. |
| Shift Security Left with DevSecOps Tools | Retailers using GitHub Advanced Security caught a vulnerable Node.js dependency before it was exploited in the wild. | Catch vulnerabilities during code review to prevent downstream deployment risks. |
| Embrace Automated Security Testing | SonarQube uncovered legacy SQL injection vectors in a gaming app's admin panel, live for years without detection. | Use static analysis and SAST tools to find hidden vulnerabilities, especially in legacy codebases. |
Conclusion
Security belongs to everyone—not just the security team. These breach stories underscore how simple flaws can escalate into large-scale incidents. Stay tuned as we dive deeper into OWASP Top 10, secure design principles, and coding practices that make software resilient from the ground up.
Optional Enhancements
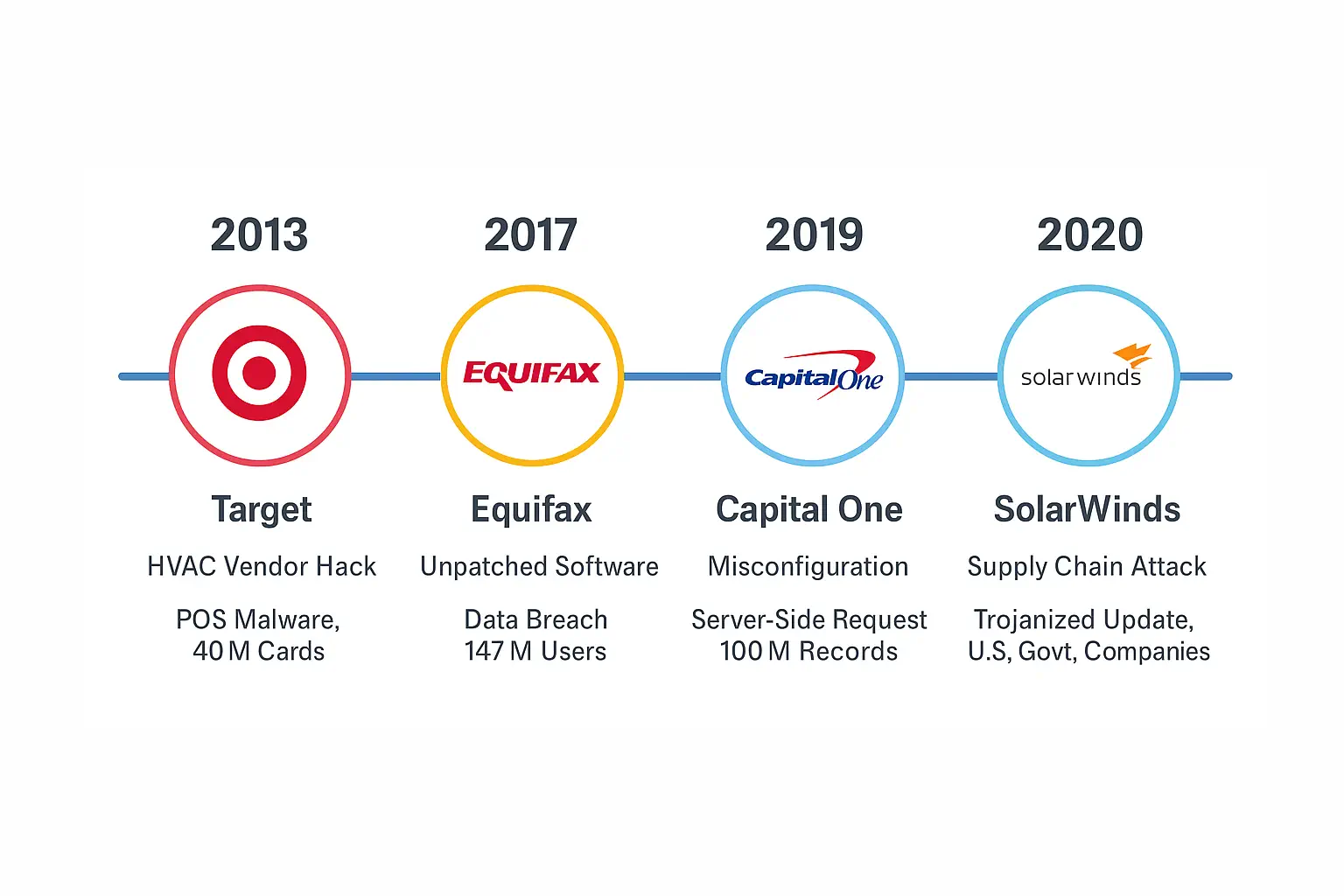
Timeline of Breaches
- 2013: Target
- 2017: Equifax
- 2019: Capital One
- 2020: SolarWinds
Quote
“Security is not a feature, it's a mindset.” — Gene Spafford
Breach vs. Prevention Cost
Investing in security is not just about compliance; it’s about protecting your users and your business. The cost of a breach far outweighs the investment in prevention. Remember: An ounce of prevention is worth a pound of cure.
The True Cost: Breach vs. Prevention
💸 Average cost of a breach (IBM 2023): $4.45M
🛡 Annual cost of implementing DevSecOps: Less than $100K
The **smartest investment** in security isn’t post-breach recovery—it’s prevention.

Final Takeaway
Security belongs to everyone—not just the security team. Stay tuned for insights into OWASP Top 10, secure coding principles, and DevSecOps strategies.
Remember: An ounce of prevention is worth a pound of cure. Investing in security is not just about compliance; it’s about protecting your users and your business.

